Rogue AP Detection - PCI DSS Compliance
The Payment Card Industry Data Security Standard 4.0 Requirement 11.2 specifically states that wireless access points are to be identified and monitored, and unauthorized access points are to be addressed. Requirement 11.2.1 states that authorized and unauthorized wireless access points are managed as follows:
- The presence of wireless (Wi-Fi) access points is tested for,
- All authorized and unauthorized wireless access points are detected and identified,
- Testing, detection, and identification occurs at least once every three months.
- If automated monitoring is used, personnel are notified via generated alerts.
More information from PCI DSS 4 Requirement 11.2.1:
Purpose: Implementation and/or exploitation of wireless technology within a network are common paths for malicious users to gain unauthorized access to the network and cardholder data.
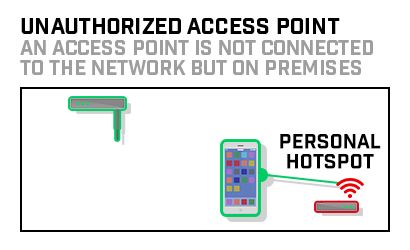
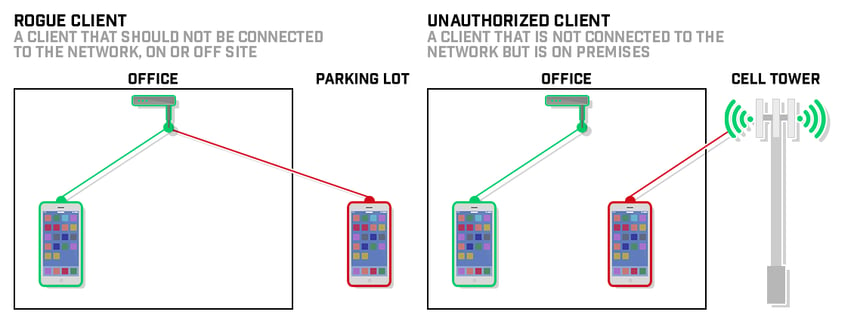
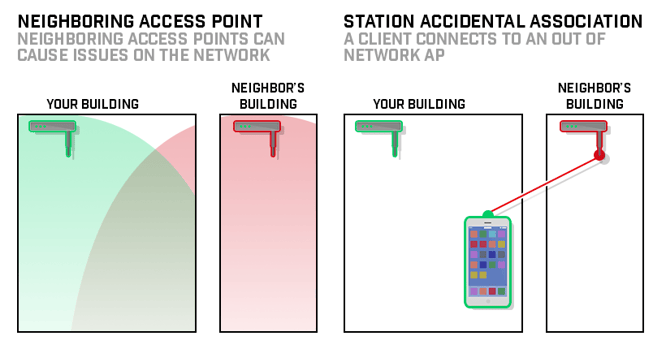
Unauthorized wireless devices could be hidden within or attached to a computer or other system component. These devices could also be attached directly to a network port, to a network device such as a switch or router, or inserted as a wireless interface card inside a system component. If a wireless device or network is installed without a company’s knowledge, it can allow an attacker to enter the network easily and “invisibly.”
Detecting and removing such unauthorized access points reduces the duration and likelihood of such devices being leveraged for an attack.
Good Practice: The size and complexity of an environment will dictate the appropriate tools and processes to be used to provide sufficient assurance that a rogue wireless access point has not been installed in the environment. For example, performing a detailed physical inspection of a single stand-alone retail kiosk in a shopping mall, where all communication components are contained within tamper-resistant and tamper-evident casings, may be sufficient to provide assurance that a rogue wireless access point has not been attached or installed. However, in an environment with multiple nodes (such as in a large retail store, call center, server room or data center), detailed physical inspection can be difficult. In this case, multiple methods may be combined, such as performing physical system inspections in conjunction with the results of a wireless analyzer.
Click here to read more about PCI DSS 4.0 and rogue device security threats.